
Drop Your Enquiries Here!
Please fill in your details below and we will contact you as soon as possible.
__________
Today, companies encounter two counteract demands. One is to leverage the reach and flexibility of IP networks to achieve an effective business environment. The other is to safeguard these networks from any potential threats of the Internet.
To grow your business, disregarding any business opportunities and threats is not an option. It is necessary to take on a proactive stance and execute the apt technologies and strategies to strengthen and safeguard your network.
ACM offers a comprehensive range of Security Services that are beneficial to you to leverage the boundless opportunities that IP networks and the Internet have to offer while alleviating network security threats.
__________
The most powerful and efficient approach to undertake any security challenges is through layered security and “defence-in-depth” strategies. To lower the security risk, companies should not compromise on their network security and should look across all systems and operational procedures to ascertain reliable security technology and practices. For the benefits of our customers, ACM deploys security services in a diversity of layers that includes:
As network security is an ever-shifting target, it is crucial for companies to apprehend and make an inventory of what competencies are managed in-house. Also, they need to determine what expertise is required from external resources. Furthermore, a single technology or system is unable to overcome any network security challenges. Customers have to conduct regular checks and adjustment to their network security to counterattack the changing landscape of menaces. ACM marries both industry top-notch security technology and specialised security experts to assist the enterprise in dealing with selective outsourcing security tasks.
Instead of protecting and surrounding the customer networks like a castle with one entrance, ACM safeguards the networks at multiple levels with utmost care. We apply the same “defence-in-depth” strategy to secure your data and infrastructure so that you can be worry-free.
Security Management
Security management’s goal is to assist you in creating an IT environment where you have constant access to accurate data. We help to protect
your data from unauthorised access and modifications while maintaining the highest possible data availability at all times.
Businesses are proactively searching for ways to eliminate unnecessary networking cost and to boost employee work productivity through the usage of new technologies. When it comes to a great network and high-speed connectivity to the latest business applications, ACM’s Managed VPN solutions is your best selection.
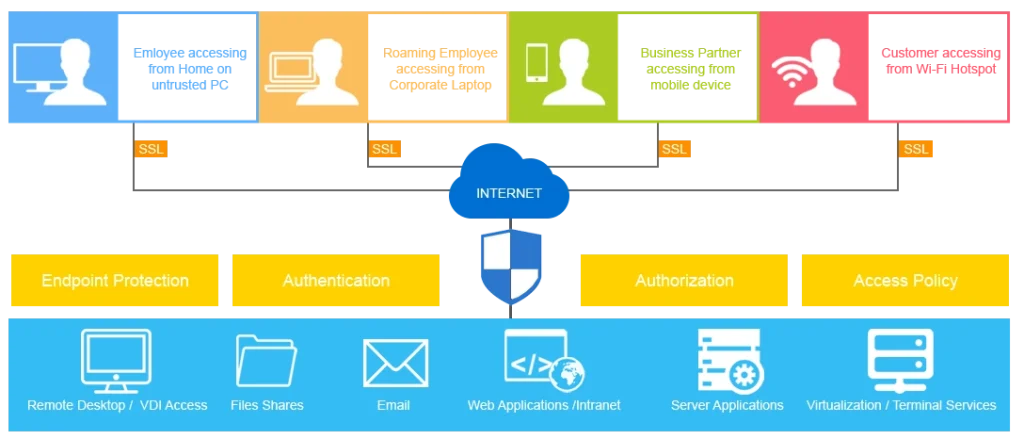
Our distinguished IP VPN solutions incorporate both MPLS routing and QoS technology with cost-efficient broadband access to attain more bandwidth, performance and flexibility at only a small fraction of the cost of legacy networks. Thus, they are the most ideal solution for high-performance driven applications like VoIP and video-conferencing.
We have a variety of access and security technologies solution that specifically cater accordingly to your business requirements. ACM promises to take on full accountability for the availability and performance of your network through 24/7 monitoring and customer servicing support.
One Seamless Solution For The Distributed Enterprise
Network VPN solutions are designed to pair up with our Remote Access VPN solutions to connect all your remote users and sites simply through a single seamlessly integrated platform.
Our SSL and IPSec-to-MPLS integration technology permit us to effectively “map” SSL and IPSec tunnels from remote users directly into your MPLS VPN network.
We also utilise the same technology to provide business partners with secure access when connected to the existing Internet. The result is an extensive Intranet and Extranet platform that permits your business to leverage the latest productive-strengthening applications.
Looking to connect your organization and headquarters? ACM offers great flexibility and high-intensity performance and security you need:
Flexibility – Pick from an extensive selection of access technology, security, bandwidth levels, management options and applications that fits your requirements.
Premium Level of Performance – ACM’s MPLS network is designed for the most particular customer voice, video and data applications.
Utmost Security – ACM’s multiple security support options apply “defence-in-depth” strategies throughout the configuration of your network.
MPLS VPNs – Regulating high-geared network connectivity and privacy with broadband access to obtain optimum coverage, quality and service.
IPSec VPNs – Ensure secured data security and network connectivity from any possible Internet connectivity.
Excessive Options – The demand and receive fault-tolerant network connectivity.

Please fill in your details below and we will contact you as soon as possible.